
Unfortunately, the trend of Google Play has been eliminating applications for their malicious content, and all this in recent months. What was news before is now something to constantly deal with, since they are viruses that can be anywhere, even in programs that have a reputation in the community. However, it is something that we can partly avoid if we know tools to detect apps with malware.
And there is room for hope if users are increasingly better informed when it comes to knowing what they download for their smartphone. Obviously, it has to be a joint work with the big G, which with Google Play Protect mainly alleviates this problem, but must continue to improve its security system. We, for our part, are going to put at the service of the whole world some tricks to detect these malicious apps.
Beware of permits
It is something that we have already repeated on several occasions, but it never hurts to remember it. What the latest batch of applications that Google Play has had to eliminate have in common are those that perform useful functions, such as cleaning tools or flashlights. In the case of the latter, you have to be very careful, since they ask for permits that are not really necessary for their operation, like sending SMS.
And the consequences can be serious, from the massive appearance of advertising while using the flashlight, to subscribing to a premium SMS service that generates additional costs on the bill. Fortunately, most devices have this tool incorporated, so it will be necessary to download an external app.
Avoid downloading alternatives that are actually copies
Although it also occurs in applications, it is something more common in games, since copies and clones of mythical titles emerge such as Solitaire or Tetris, or the most current ones such as Clash Royale, Candy Crush and a long etcetera. They are copies that seek something more than the fun of the players, rather personal or financial interests, although they are not all that do.
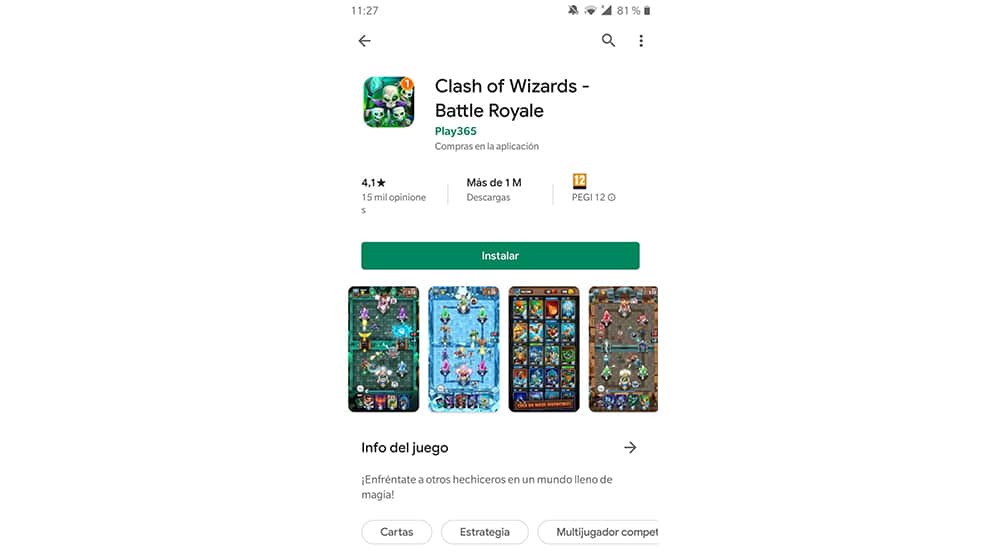
In addition, they tend to have a large number of downloads and a good rating, so, in view of the user, it makes it more reliable for installation. Really, all those figures are inflated by artificial clicks to get a good score and position itself among the top results of the Google Play Store search engine, something that the company must also improve.
Developer suspicion
Another effective measure, which is closely related to the previous point, is to look at where the app or game in question comes from. It is something that most users do not usually do, we believe that it is a very little relevant detail, but it is not like that. Currently, we can see all the developer's projects with a simple click.
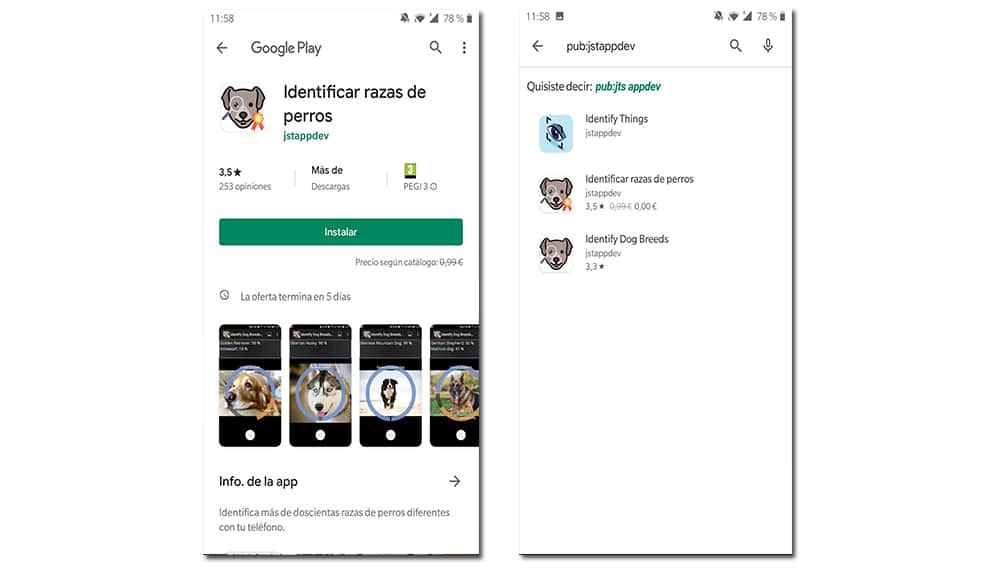
Unless it is an app heavily promoted by the media, thus confirming its reliability, the majority of developers who have only released an application or a game are already a sign of suspicion. They are companies with little diffusion in the community and that lack opinions to know their real intentions, as happens in the example shown just a few lines above.
Stay informed
To be aware of the arrival of a virus or malware to the Google store, it is best to be aware of specialized media. The Mountain View company does not go with a bell announcing the infected programs so as not to create an alarm, but removes them directly from the store to avoid more downloads, although the problem will continue to reside in users who have them installed on their devices. For this reason, it is advisable to take a look at these specialized sites sporadically, Incidentally, they are the ones that usually report these pests, so here are some exponents of the sector: